Microservice-Auth Service (3)
¶Microservice (3)
- Setup tsconfig with
tsc —init index.tsDockerfileDockerignoreauth-depl.yamlingress-srv.yamlskaffold.ymlskaffold dev
As we are using microservice architecture, we need to standardize the way of transmitting errors to clients.
We can create a specific error handler (with four params) to handle all errors!
1 | |
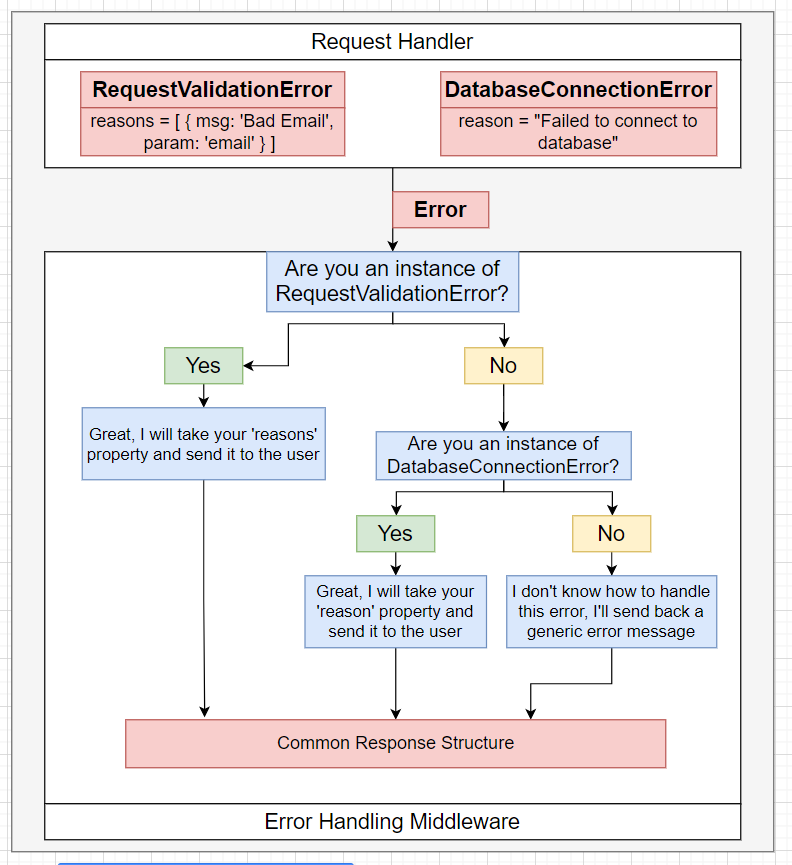
We can use abstract class that force the custom error class to implement several functionalities
Check the code base for details
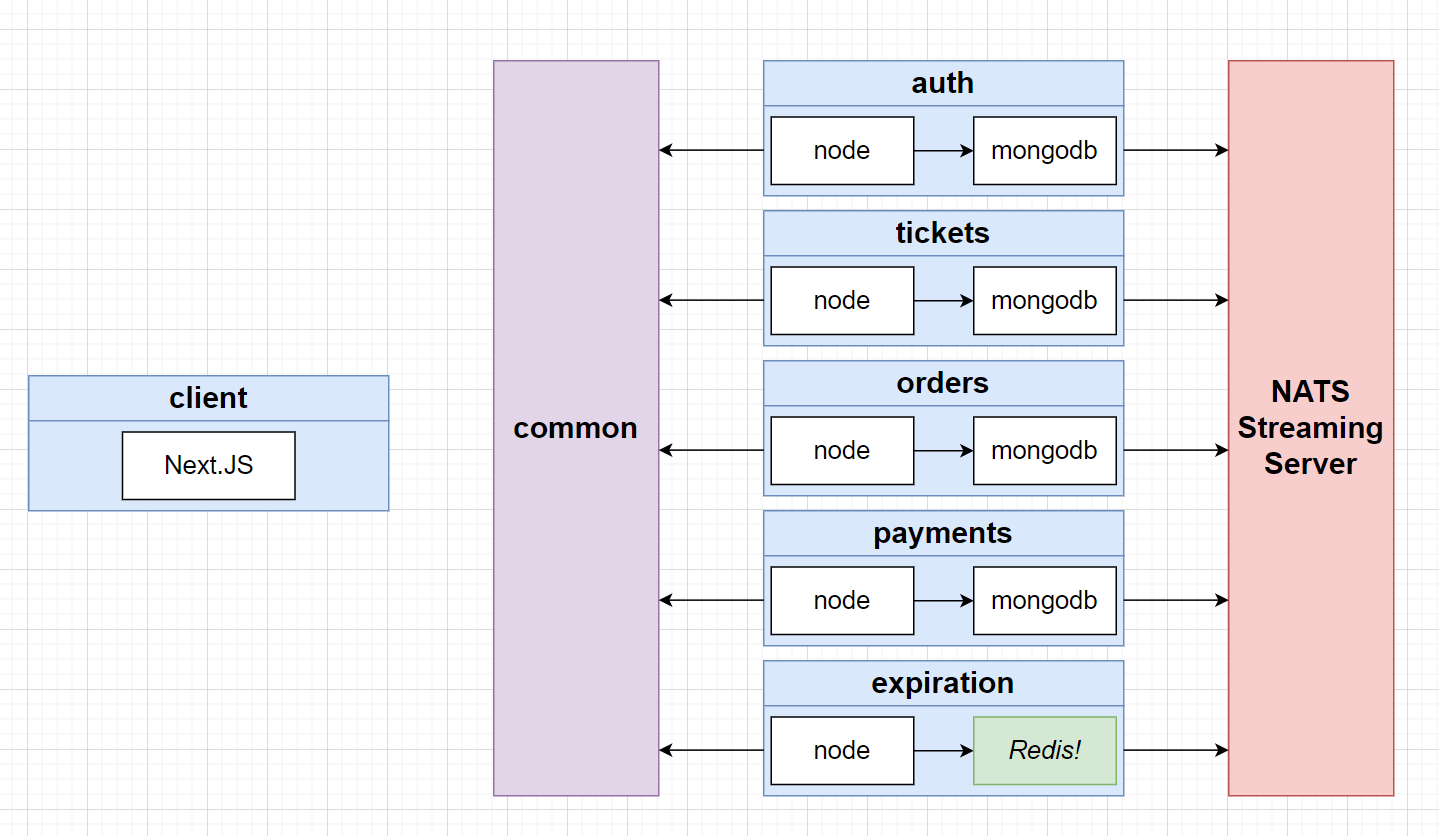
¶MongoDB
We will create One MongoDB for one service
这里和microservice没太大关系, 具体看代码
注意,我们需要用
import "express-async-errors"; 不然在express里的 async 函数无法throw error!
¶Authentication
How to authenticate can be a difficult problem in Microservices
-
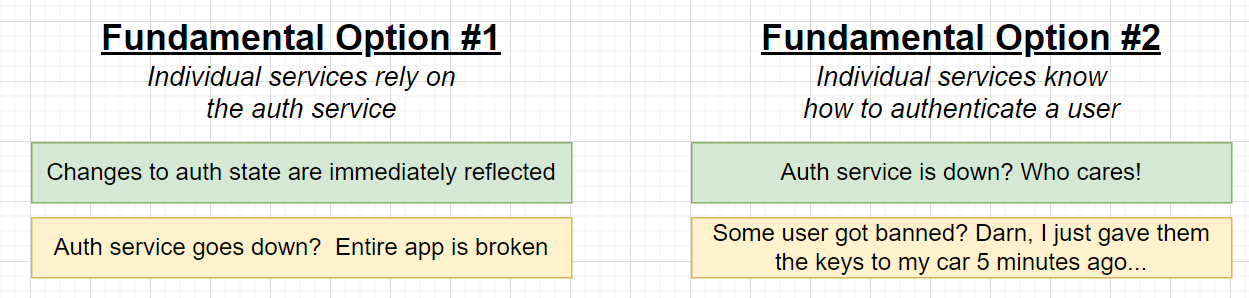
Sync request (No Event Bus) with a centralized auth service:
BAD:
- coupling
- single break point of the whole system
-
Each service have its own JWT/Cookie to check
BAD:
- Hard to implement
- cannot instantly reflect the current status of a user in all services as user has 100% control of the token!
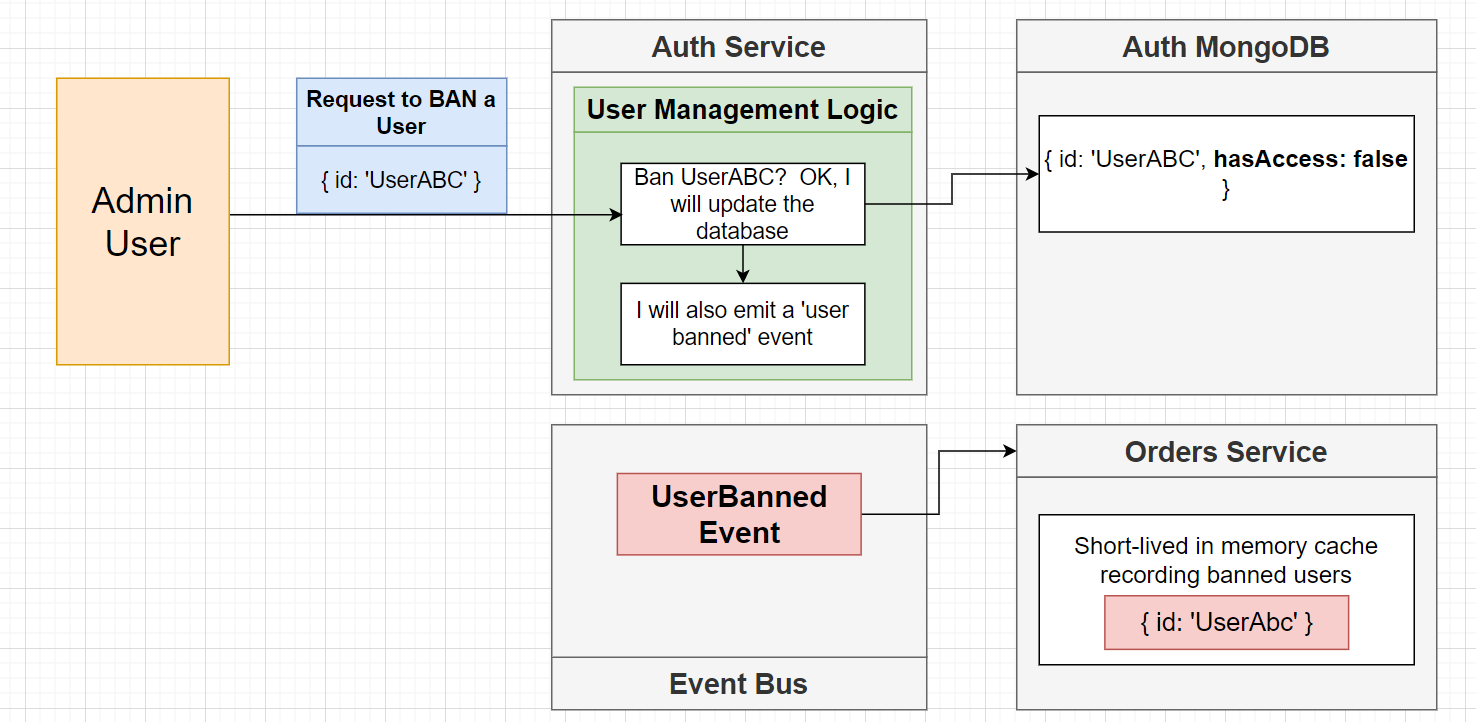
Right now ,our strategy is as follow:
- user login through auth service, issued with a 15 mins of token
- if a admin user sends a request to ban a user, a
UserBannedevent is emitted to Event Bus - all services will be listening to this event, and store the banned user into its own
rediscache for 15 mins - If a user reached a service, service can know if it is allowed through
redis!
¶JWT/Cookie
Cookie is sent through Set-Cookie and managed by the browser. Server side can normally be guaranteed requests will have to the access of the settled cookie
JWT is handled by client code but not the browser. JWT token is sent through header every time of the request.
Cookie’s expiration date can be ignored as it is handled by the browser.
JWT is a more common and easy to handle technique as it is understood by other languages easily.
One important advantage to use microservice is that services can be implemented by different languages!
Because of server side rendering, the first time a user request to a URL cannot attach any authentication information as normal SPA can do. Therefore, we must store the JWT in cookie! JWT itself is not secret. However, we can use Signing key to check if a JWT is verified or not.
We need cookie-session to store session data in cookie! , JWT is naturally temper-resistant,
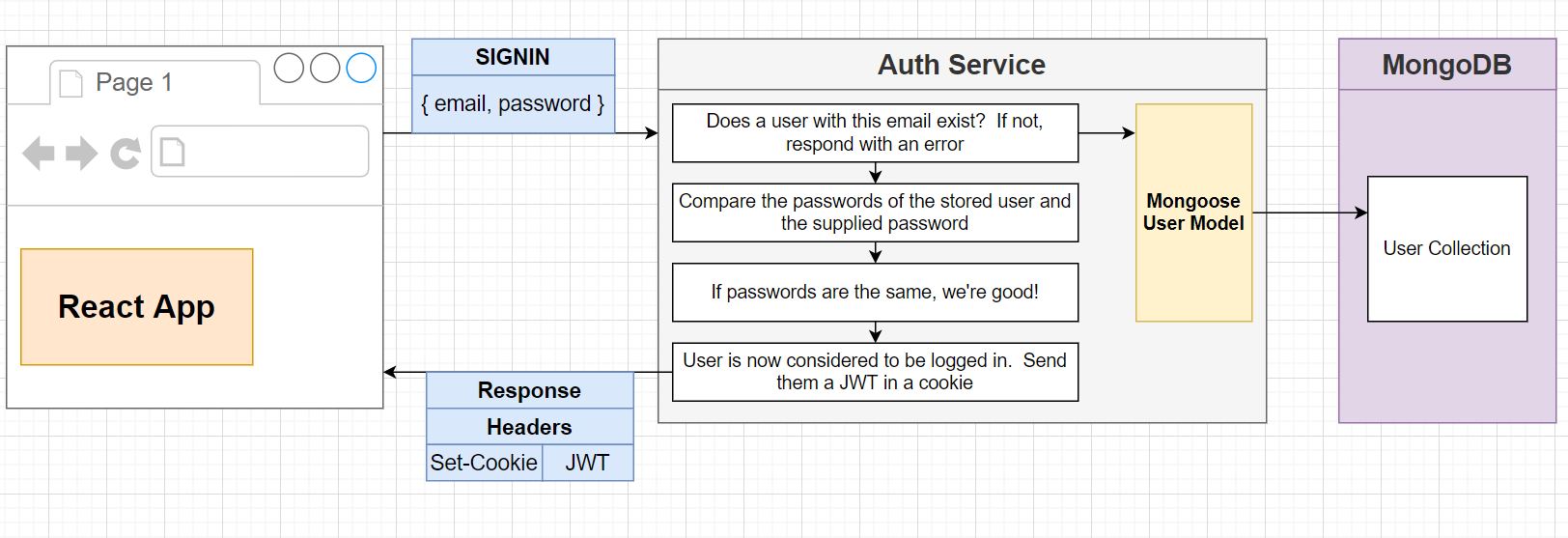
才发现,_id 会被 mongodb 自动转化为 property idof string type
¶Secrete in k8s
Secret object can be created and share through pods
Secret object can then be treated as env variable for all pods.
Imperative approach to create a secret object!
1 | |
We then can put the secret into the container through the Deployment
1 | |
¶_id
JSON.stringify() can be overwritten by toJSON() function in the object
¶Testing
Main quesstion: What’s the scope of our tests?
- Single middleware → Unit test
- Single pipe
- The whole service
- different services?
没写这,如果要用直接看视频吧
We need to split the logic of Express App and Start Up into two files
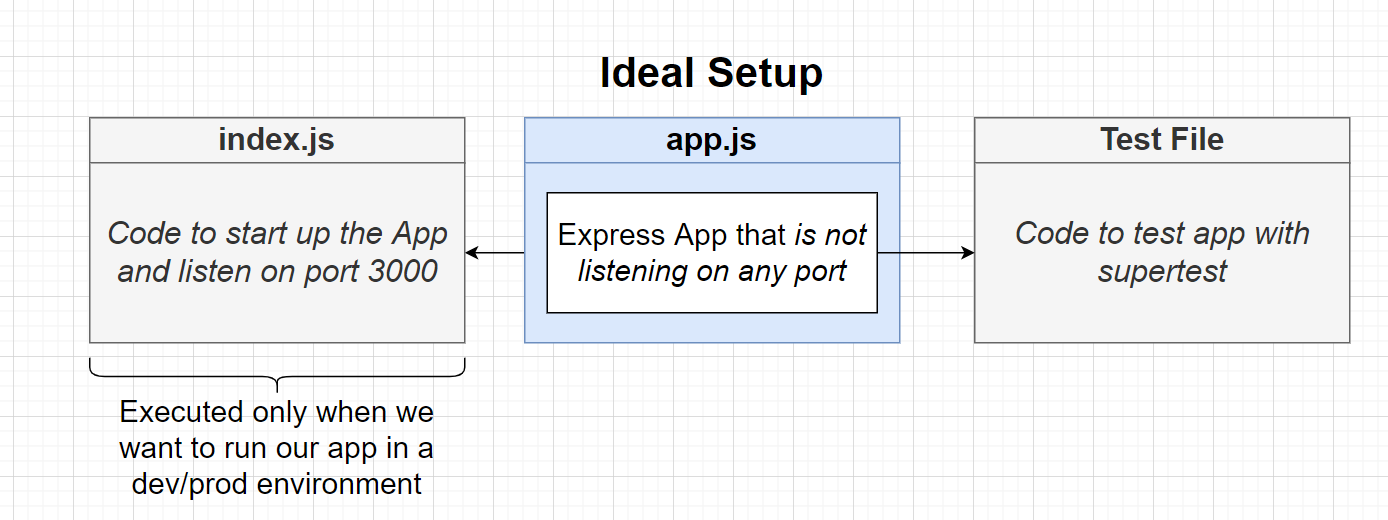
See code for details please!
1 | |
总结以下本小结:
One MongoDB for each service!
import "express-async-errors";不然在express里的async函数无法throwerror!Authentication can be difficult:
- Sync request (No Event Bus) with a centralized auth service:
- coupling
- single break point of the whole system
- Each service have its own JWT/Cookie to check
- Hard to implement
- cannot instantly reflect the current status of a user in all services as user has 100% control of the token
- Sync request (No Event Bus) with a centralized auth service:
Our stategy:
Right now ,our strategy is as follow:
- user login through auth service, issued with a 15 mins of token
- if a admin user sends a request to ban a user, a
UserBannedevent is emitted to Event Bus - all services will be listening to this event, and store the banned user into its own
rediscache for 15 mins - If a user reached a service, service can know if it is allowed through
redis!
JSON.stringify()can be overwritten bytoJSON()function in the object才发现,
_id会被 mongodb 自动转化为 propertyidof string typeTest 看代码
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!